通用ShellCode学习笔记——win7中获得LoadLibrary地址
时间:2010-09-19 来源:zodiac21
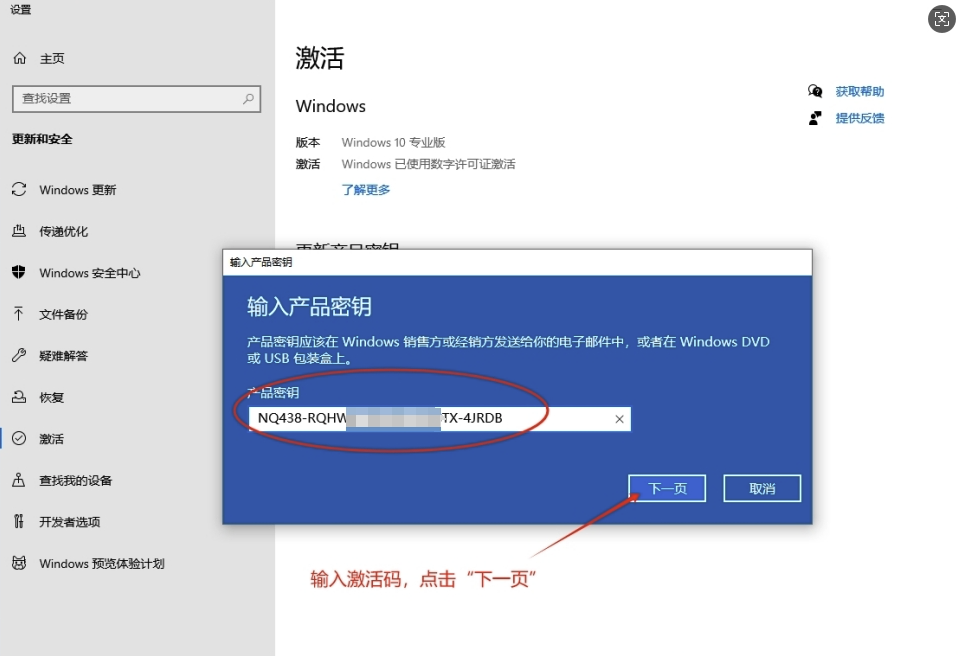
win7中使用了LoadLibraryExA,不能通过调用GetProcAddress来获得
代码如下:
int main()
{
__asm
{
push ebp;
sub esp,100;预留函数地址空间
mov ebp,esp;
mov eax,fs:0x30;
mov eax,[eax+0x0c];
mov esi,[eax+0x1c]
lodsd
mov edi,[eax+0x08];获取kernel32
mov eax,[edi+3ch];pe header
mov edx,[edi+eax+78h]
add edx,edi
mov ecx,[edx+18h];number of functions
mov ebx,[edx+20h]
add ebx,edi;AddressOfName
search:
dec ecx
mov esi,[ebx+ecx*4]
add esi,edi;
mov eax,0x50746547;PteG("GetP")
cmp [esi],eax
jne search
mov eax,0x41636f72;Acor("rocA")
cmp [esi+4],eax
jne search
mov ebx,[edx+24h]
add ebx,edi;index address
mov cx,[ebx+ecx*2]
mov ebx,[edx+1ch]
add ebx,edi
mov eax,[ebx+ecx*4]
add eax,edi
mov [ebp+76],eax;将GetProcAddress地址存在ebp+76中
push DWORD PTR 0x00004178
push DWORD PTR 0x45797261;Ayra("aryE")
push DWORD PTR 0x7262694c;rbiL("Libr")
push DWORD PTR 0x64616f4c;daoL("Load")
push esp
push edi
call [ebp+76]
mov [ebp+80],eax;将LoadLibraryA地址存在ebp+80中
/*
;构造函数名
push dword ptr 0xAAAAAAAA
push dword ptr 0xAAAAAAAA
push dword ptr 0xAAAAAAAA
.
.
.
push esp
push edi;kernel32地址
call [ebp+76];调用GetProcAddress
mov [ebp+X],eax;该函数地址存放在ebp+X中
*/
}
return 0;
}
相关阅读 更多 +