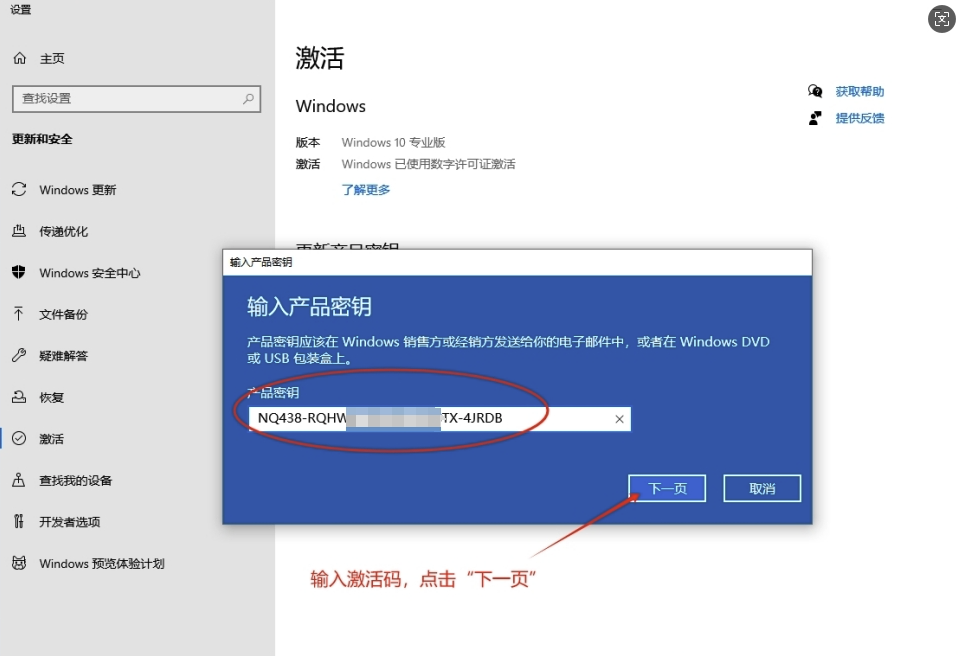
检测局域网内的开着的电脑
时间:2006-02-26 来源:cnscn2008
#!/bin/sh
#Name: findcomputer.sh
#
#Author: cnscn
#检测局域网内的开着的电脑(---不知这样做方法不好,请大家指正)
#
#
for i in {1..255}
do
nmap -nsP 192.168.0.$i
echo
done
or
nmap -sP 192.168.0.0/24
============================================
//检测开着的电脑
[root@localhost ~]# ./findcomputer.sh | grep "appears to be up"
Host 192.168.0.1 appears to be up.
Host 192.168.0.5 appears to be up.
Host 192.168.0.40 appears to be up.
Host 192.168.0.100 appears to be up.
Host 192.168.0.246 appears to be up.
============================================
//检测,40开着的端口
[root@localhost ~]# nmap -v 192.168.0.40
Starting nmap 3.70 ( http://www.insecure.org/nmap/ ) at 2006-02-26 11:32 CST
Initiating SYN Stealth Scan against 192.168.0.40 [1660 ports] at 11:32
Discovered open port 5000/tcp on 192.168.0.40
Discovered open port 135/tcp on 192.168.0.40
Discovered open port 445/tcp on 192.168.0.40
Discovered open port 1025/tcp on 192.168.0.40
Discovered open port 139/tcp on 192.168.0.40
The SYN Stealth Scan took 0.40s to scan 1660 total ports.
Host 192.168.0.40 appears to be up ... good.
Interesting ports on 192.168.0.40:
(The 1655 ports scanned but not shown below are in state: closed)
PORT STATE SERVICE
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
1025/tcp open NFS-or-IIS
5000/tcp open UPnP
MAC Address: 00:07:95:AF:97:AE (Elitegroup Computer System Co. (ECS))
Nmap run completed -- 1 IP address (1 host up) scanned in 11.232 seconds
#Name: findcomputer.sh
#
#Author: cnscn
#检测局域网内的开着的电脑(---不知这样做方法不好,请大家指正)
#
#
for i in {1..255}
do
nmap -nsP 192.168.0.$i
echo
done
or
nmap -sP 192.168.0.0/24
============================================
//检测开着的电脑
[root@localhost ~]# ./findcomputer.sh | grep "appears to be up"
Host 192.168.0.1 appears to be up.
Host 192.168.0.5 appears to be up.
Host 192.168.0.40 appears to be up.
Host 192.168.0.100 appears to be up.
Host 192.168.0.246 appears to be up.
============================================
//检测,40开着的端口
[root@localhost ~]# nmap -v 192.168.0.40
Starting nmap 3.70 ( http://www.insecure.org/nmap/ ) at 2006-02-26 11:32 CST
Initiating SYN Stealth Scan against 192.168.0.40 [1660 ports] at 11:32
Discovered open port 5000/tcp on 192.168.0.40
Discovered open port 135/tcp on 192.168.0.40
Discovered open port 445/tcp on 192.168.0.40
Discovered open port 1025/tcp on 192.168.0.40
Discovered open port 139/tcp on 192.168.0.40
The SYN Stealth Scan took 0.40s to scan 1660 total ports.
Host 192.168.0.40 appears to be up ... good.
Interesting ports on 192.168.0.40:
(The 1655 ports scanned but not shown below are in state: closed)
PORT STATE SERVICE
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
1025/tcp open NFS-or-IIS
5000/tcp open UPnP
MAC Address: 00:07:95:AF:97:AE (Elitegroup Computer System Co. (ECS))
Nmap run completed -- 1 IP address (1 host up) scanned in 11.232 seconds
相关阅读 更多 +